What is IP address and How it works?
Every computer has an IP which is called Internet Protocol. When the people connect to the Internet, their IP address is disseminating to any server, and if they logged on that server, then the problem can occur. IP address just helps to identify the user personally. So hackers identify that IP address and they monitor their activity on a regular basis. These hackers steal user identity or other personal information. Your Internet Provider is tracking your online activities! Hide your IP ADDRESS Now!
The Difference Between Local and Public IP Address
How to Mask your IP address
There are many ways to help you by changing your IP address and geographical location when using the internet. Individuals tend to want to change their IP address for many reasons, in most cases, it is for security and privacy, as well as anonymity. A simple Google search will give you plenty of results on how to change or hide your IP address, and the initial result you’ll see will be proxy servers, virtual private networks and the onion router (TOR).
Using Proxy Server
Proxy servers act as a mediator between your computer and another connection on the internet, such as a web browser. As your connection is being streamed through another computer/server, your IP address is hidden from the rest of the public and, instead, the IP address of the proxy server is shown. This allows you to also appear as if you are signaling from another geographical location, and both of these features give you security and privacy when surfing the web. Proxy servers come in many shapes and sizes and do not have encrypted pathways as they are used by hundreds and thousands of users at a time. Because of this, proxy servers can only handle one application at a time, such as a web browser, leaving your email and file uploads/downloads open to keen eyes. There are many types of proxies available. However, it is imperative to know the right process.
Web Proxy
The user should enter the address of the website in the URL box which they want to visit. If this site is not working properly, you should already use the different proxy sites online.
This kind of proxy is known as a web proxy. It provides privacy while surfing on the Internet. Moreover, it hides the original IP address of the user. An Anonymous Proxy Server is difficult to track. There are cookies that track the user every day. There are many anonymous proxy sites that protect the user when they surf the net. However, it is very much important to identify the right kind of proxy server. There is also an atrocious proxy server that can harm the computer. The good quality anonymous proxy servers will provide an SSL which is called Secure Sockets Layer. It helps to block the eavesdroppers. This kind of proxy server is very much capable of eliminating the cookies.
Open proxies
There is a diverse list of proxy sites as IP:Port. However, it important to know this type of proxies,
There are many proxy list websites where the people can use the proxies, But Not all proxies List are good. So it is very much necessary to find the right proxy sites. Some Open proxies may not safe to use, the proxy server may store you on your billing information or online passport. Using an open proxy that is shared with all users, so the speed of the proxy is really slow.
Dedicated Proxies
A Dedicated proxy server has similar benefits and limitations to that of regular proxy servers, but do vary significantly. As you are the only one using the server, you are preventing yourself from being subject to the consequences of someone else’s actions, and Dedicated proxies tend to be faster as they are not subject to user congestion. However, Dedicated proxies tend to more expensive than your standard public proxy and they are difficult to find for free, you can try cheap shared proxies if you can not afford the private proxy.
Residential Proxies
The Residential proxy server is a proxy gateway that content to Residential/home internet connections, The Residential IP proxies are more trusted able than the datacenter proxies! The Residential IP Proxy become more and more popular! You can use the proxies for web scraping and social automation! The downside is the slow speed when compared to the private proxy.
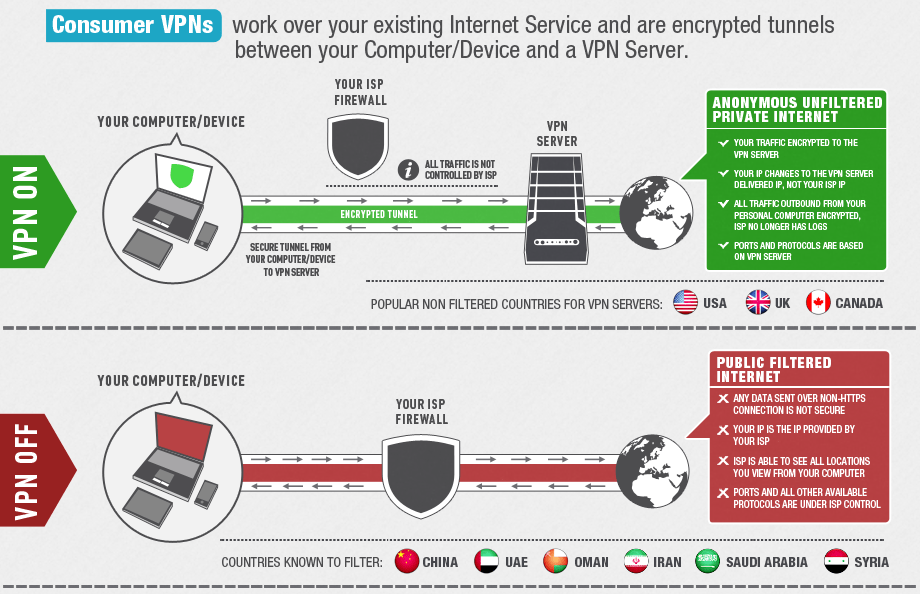
Using VPN
VPN achieves the same result as proxy servers as they can also hide your IP address and geographical location. However, they differ massively and do the job even better. VPN doesn’t just capture one application (such as a web browser), but essentially captures you’re entire internet connection and every application on your computer, such as your email, and reroutes your ISP. This gives the connection between your computer and the server military-grade encryption, giving you the luxury to surf the internet in complete privacy and security. This encryption also gives you privacy from ISP and Governments who might want to see what you’re up too. The only information they will be able to obtain is that you’re connected to a VPN, that’s it. VPN can also offer faster connections depending on the provider and setup is relatively easy. There are obviously downsides to VPN, the first one being price. VPN is very expensive and much more expensive than proxy servers. In addition, although you may experience faster connections, VPN can become slow at peak times. There is also the issue of logs. If the network provider keeps logs of what goes on in their network, ISP and Governments can obtain these logs on request.
Cheap But Good VPN Services – Compare & Find Your Ideal Cheap VPN! The Best VPN to use in the USA (Get US IP address to Steam) Which VPN is the Fastest VPN?
Using Tor
TOR stands for The Onion Router and is essentially a series of virtual tunnels that act similarly to a proxy server. The difference is instead of your connection being pasted through just one computer, your connection is bounced through several computers, creating layered protection. Hence why it’s called ‘the Onion Router’. As your connection is passed through different computers, your IP address is hidden and your geographical location is hidden also. The computers who are involved in the process are known as TOR relays and there are three types: middle relays, end relays, and bridges. The initial connections are all encrypted and the final connection is not as it is usually considered to be ‘in the clear’. The biggest issue for using TOR is performance-related issues, as streaming your connection through 3 computer systems can result in slower speeds. In addition, Governments are aware of the power of TOR and end relays (the final computer in the chain) often attract the attention of law enforcement agencies and sometimes receive copyright notices.
Conclusion
There are many ways to hide your IP address from the rest of the internet, and they all vary in process and ability. Proxy servers offer the most basic and cheapest way to bounce your connection through one computer to another connection or application on the internet, whereas VPN captures your entire connection and all applications on your computer giving you military-grade protection. TOR offers a combination of the two, by sending your connection through multiple computers with encrypted pathways. They all have their own benefits and limitations and it is up to you to choose the correct one for you. Hopefully, this article has given you some insight into the ways you can hide your IP address and thanks for reading.